Inside AuthNull — Building Intelligent, Conditional Access with AI + Agents

Conditional Access by AuthNull
Conditional access is a modern security framework that dynamically controls access to systems and data based on real-time context — such as user identity, device posture, location, time of access, and behavioral signals. Instead of relying on static rules or binary allow/deny logic, conditional access adapts to evolving risk conditions, ensuring that the right people get the right level of access under the right circumstances. It’s the foundation of zero trust security — where trust is earned continuously, not assumed.
Conditional access, RBAC and ABAC
Conditional access, Role-Based Access Control (RBAC), and Attribute-Based Access Control (ABAC) each represent different approaches to managing access — but they serve distinct purposes. RBAC assigns permissions based on a user’s role within the organization (e.g., “engineer” or “HR”), offering simplicity but limited flexibility. ABAC expands on this by evaluating a broader set of attributes — such as department, clearance level, device type, or time of access — to make access decisions. Conditional access goes a step further: it continuously evaluates context and risk in real time (such as geolocation, network trust, behavioral anomalies, or device hygiene) to grant, deny, or escalate access dynamically. While RBAC and ABAC focus on who the user is and what attributes they present, conditional access focuses on when and how access is being attempted — making it essential for implementing adaptive, zero trust security.
The Problem with the Old Playbook
We’ve talked to dozens of security teams — from scrappy startups to large enterprises — and they all said the same thing: traditional conditional access rules just don’t cut it anymore.
“Only allow access during office hours.”
“Block logins from overseas.”
“Force MFA if login fails 3 times.”
They work, until they don’t.
Why? Because those systems don’t learn. They don’t adapt. They don’t know the difference between a tired engineer logging in from a coffee shop and an actual attacker.
They react. But they don’t reason.
Rewriting the Rules with AuthNull
At AuthNull, we asked: What if conditional access could think?
What if it didn’t just enforce rules — but understood them?
That’s the story of how we built our intelligent, agent-powered Conditional Access Engine. And it all starts with a single question: What does trust look like in motion?
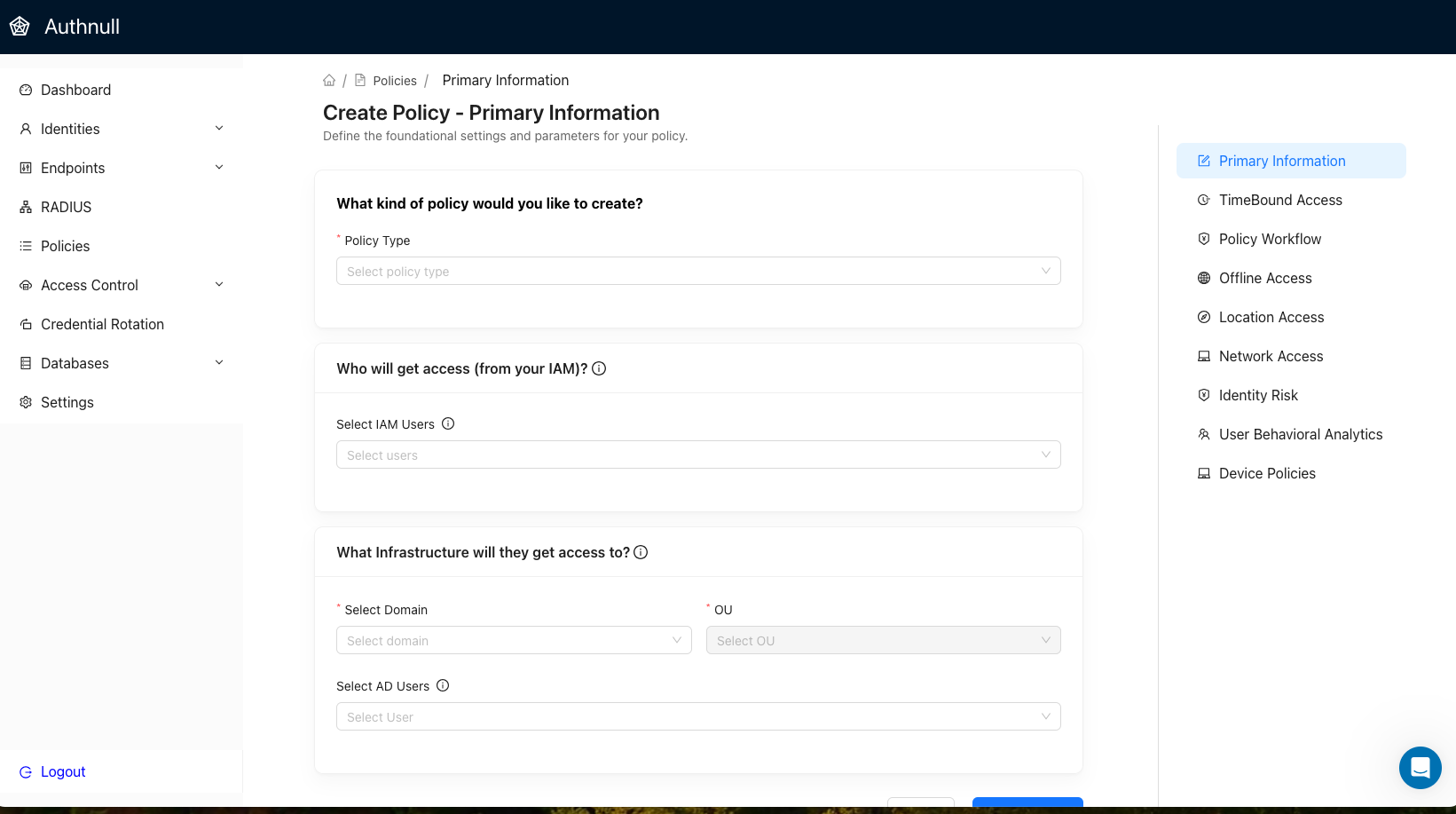
Setting the Stage: Defining a Policy
Let’s follow Maya, a security admin at a mid-size SaaS company. She wants to create a policy for contractors who only need database access during a scheduled upgrade window — and only from the U.S.
With most tools, Maya would have to stitch together rules across OS platforms, IDPs, and databases.
With AuthNull, she opens a clean, modular UI. No guesswork. No scripting.
She fills out the basics: target infrastructure (a Postgres DB cluster), user group (contractors), and timeframe (midnight to 4am UTC).
Then she layers in geofencing: U.S. only.
Network access: only from the corporate VPN.
And finally — dynamic risk checks. If the user’s behavior seems unusual (new device, location mismatch, MFA fails), block the session immediately.
It took her five minutes. No code. No misconfigurations. But the policy? It’s airtight.
When Policies Learn, Security Scales
Maya’s team doesn’t just write policies. They teach the system how to reason.
Every login attempt across Windows, Linux, Active Directory, RADIUS, and database sessions — is logged in real time. The logs aren’t just stored. They’re analyzed. Embedded into a vector database. Pattern-matched.
A user’s IP, device ID, login time, and even MFA result — all become part of a behavioral fingerprint.
When a login request comes in, AuthNull’s engine doesn’t look at one factor. It looks at all of them. In context. Together.
If something feels “off” — the AI agents step in. They compare it to historical data. Flag it. Adjust the risk score. Suggest tighter policies. Sometimes, block the session outright.
It’s not just automation — it’s intelligent access control.
From Static Rules to a Living System
Here’s what makes AuthNull different: trust is earned. And it can be lost.
A device that consistently passes MFA and behaves normally becomes trusted. But if it suddenly starts failing logins or accessing unfamiliar services — trust is revoked.
And this isn’t happening once a week in a cron job. It’s happening in real time. Every session. Every request. Across every system.
AuthNull’s engine constantly evaluates:
Risk scores (user, session, location, network) Trust states (device, IP, behavior patterns) Policy matches (org-specific, user-specific) And based on that — it decides: allow, deny, or escalate.
But Wait — There’s a Copilot
Not everyone wants to build policies from scratch. So we built the Policy Copilot.
It’s like having a security analyst on call 24/7.
It combs through your logs. Highlights risky behavior. Suggests improvements. Even auto-generates draft policies based on real-world usage patterns — not assumptions.
You’re always in control. But you’re never alone.
The Architecture Behind It All
At the core of AuthNull’s engine are three powerful layers:
A vector database to store and compare behavior patterns A relational store for risk scoring and real-time decisions An AI policy engine that applies and recommends adaptive controls And it’s all enforced by a proxy layer that works directly at the infrastructure level — from SSH to SQL to RADIUS.
Need to approve access mid-session? Just tap yes in the AuthNull mobile wallet. It’s real-time. It’s contextual. It’s yours.
Why It Matters for Your Org
With AuthNull, security teams get:
Real-time threat blocking without waiting for a human to react Fewer false positives, so teams can focus on real risks Custom-fit policies for every team, every device, every location Lower overhead, thanks to automation that learns From lean IT teams to enterprise-scale operations, AuthNull adapts to your world — not the other way around.
What’s Next?
We’re already rolling out:
Zero Trust Posture Scores for users, devices, and networks Adaptive MFA — where low-risk sessions skip friction, and high-risk ones get flagged Deeper wallet integration for real-time approvals Because secure access should feel smart, not restrictive.
Final Word: Context Is the New Perimeter
In today’s threat landscape, access is no longer just about who — it’s about how, where, and when.
At AuthNull, we believe the best security is invisible when things are normal — and unforgiving when they’re not.
So don’t just write policies. Build a system that understands them. Learns from them. And protects you because of them.