general 26
Understanding Cyber Insurance and Its Importance
The insurance industry is adapting to help business manage risk, with cyber insurance advancing rapidly. Cyber insurance serves as a crucial safeguard for businesses facing insider cybercri...
20 password management best practices
Within the enterprise ecosystem, the task of managing passwords often falls upon the shoulders of business users, laden with significant responsibility. However, a more effective approach to mitiga...
Understanding Secrets Management and Its Importance
In a digital enterprise, various types of secrets exist. In this post, we will explore the concept of secrets management and examine the lifecycle of a secret. First, we’ll define what a secret is,...
Risk-based authentication-A pillar of a zero-trust strategy
In today’s dynamic organizational landscape, it’s evident that companies have undergone significant transformations within just a matter of years. Similarly, the introduction of n...
Top 5 Secrets Management Practices
What is Secrets Management? Secrets management is the practice of securely handling digital authentication credentials such as passwords, API keys, tokens, and other sensitive information....
Extended PAM for Integrated, Multi-Layered Cybersecurity Defense
With the growing complexity of IT systems and the increase of IAM and cybersecurity tools, effectively tackling privileged account attacks has become increasingly challenging. Why is Extended PAM ...
Privileged access Management Best Practices
The critical role of privileged accounts in managing IT environments and facilitating administrative tasks is vital for organizations to adopt PAM best practices to mitigate the risks associated wi...
Cybersecurity Incident Response Plan Template
Cyberattacks pose a constant threat, capable of disrupting businesses without notice. To withstand these inevitable threats and build cyber resilience, having robust incident response plans refined...
Cybersecurity goals-How to set and achieve them
Cybersecurity goals are critical for a cybersecurity leader The rapid increase of digital technologies and the growing sophistication of cyber threats have elevated the need to establish robust cy...
Insights into enhanced cybersecurity insurance requirements
As cyber threats continue to evolve, causing significant disruptions to businesses, the insurance industry is facing escalating expenses from ransomware attacks and struggling to manage the increas...
10 steps to prevent identity threats using privileged access
Cyber criminals steal credentials used by SaaS administrators and privileged user accounts in order to gain access to the sensitive systems. Preventing identity threats using privileged access invo...
Top 5 Benefits of Adopting a Modern Cloud-Ready PAM Solution
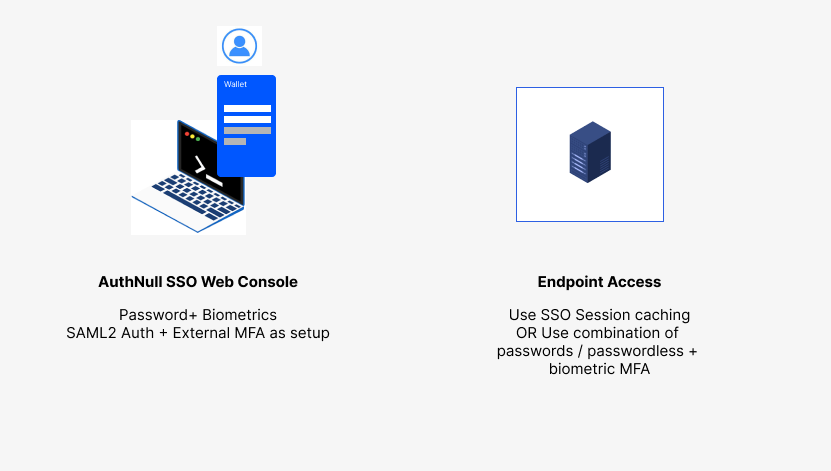
Intro to MFA Caching MFA caching is an exciting new feature that enables users to authenticate into the SSO console and use that MFA while the session is active to further disable MFA notification...

Protecting Service Account Blindspots
Protecting Service Account Blindspots Service account blind spots refer to potential vulnerabilities in the management and oversight of service accounts within an organization’s IT infrastructure....

Why you should enable MFA for your Active Directory Infrastructure
What are the threats to Active Directory? Active Directory is a critical component of many organizations’ IT infrastructure due to which it is highly targeted by cyber attackers. Some of these thr...

The Importance of Adaptive Multi-factor Authentication (MFA) for Organizations
Introduction High-profile security breaches are most common these days, such breaches exploit system login credentials of users and make their way into the company’s network. Thus, organizations t...

Importance of Privileged Access Management (PAM) for Cybersecurity Insurance
Cyberattacks are a common affair in today’s time and can be very costly due to which cyber insurance policies have been tightening their requirements to prevent financial losses. Over the past few ...

Adaptive MFA
Adaptive multi-factor authentication (MFA) is a precaution that supports contextual information and business rules to decide which authentication is best suitable for a specific user at the given s...

Mastering the Art of Safeguarding Privileged Users: Best Practices for Management and Security Master
An organization may have more than one privileged user accounts and such accounts have greater level of control and authority into the system. Thus, securing these special accounts is a must to pro...

April 2024 Release notes
AuthNull’s Policy Engine is a new feature built to by automatically identifying and creating authentication policies for privileged users. AuthNull’s Policy Engine enables a significant step towar...
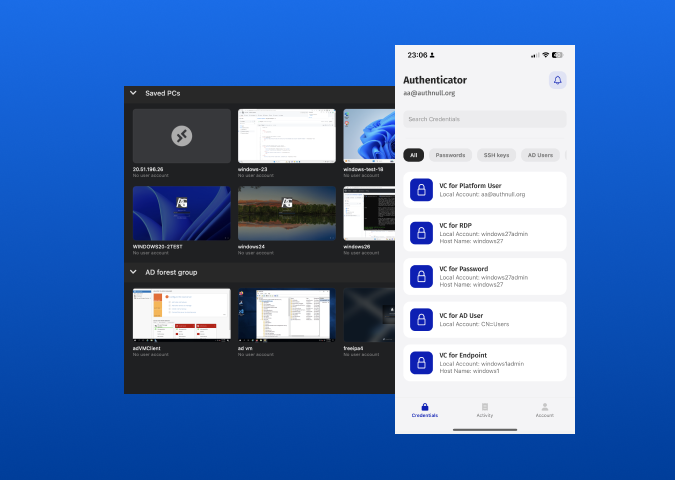
Privileged MFA
Introducing AuthNull’s latest features, empowering you to manage privileged Multi-Factor Authentication (MFA) based on your organization’s unique security posture and enabling frictionless logins. ...
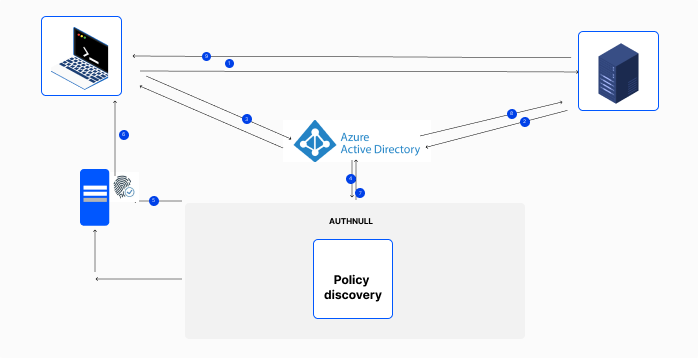
Frictionless privileged access through automated policy discovery
AuthNull’s Policy Engine is a new feature built to by automatically identifying and creating authentication policies for privileged users. AuthNull’s Policy Engine enables a significant step towar...

Navigating the FTC Safeguards Rule: A Comprehensive Guide for Financial Institutions
The Federal Trade Commission (FTC) Safeguards Rule is a set of regulations designed to protect the confidentiality and security of customer information held by financial institutions. The rule appl...

Top 5 Benefits of Adopting a Modern Cloud-Ready PAM Solution
Yangchenla Palzor Many legacy Privileged Access Management (PAM) solutions rely heavily on manual processes and are tailored for human administrators or data center environments. This makes them ...

Service accounts – discover, manage and authenticate without secrets
Service accounts are operational blind spots for IT administrators In the context of Windows operating systems, service accounts are special user accounts specifically created and used by Windows ...

FIPS Compliance: The Key to Secure Government IT Infrastructure
The federal government is responsible for protecting sensitive data, and FIPS compliance is a key part of that effort. FIPS stands for Federal Information Processing Standards, and it is a set of s...
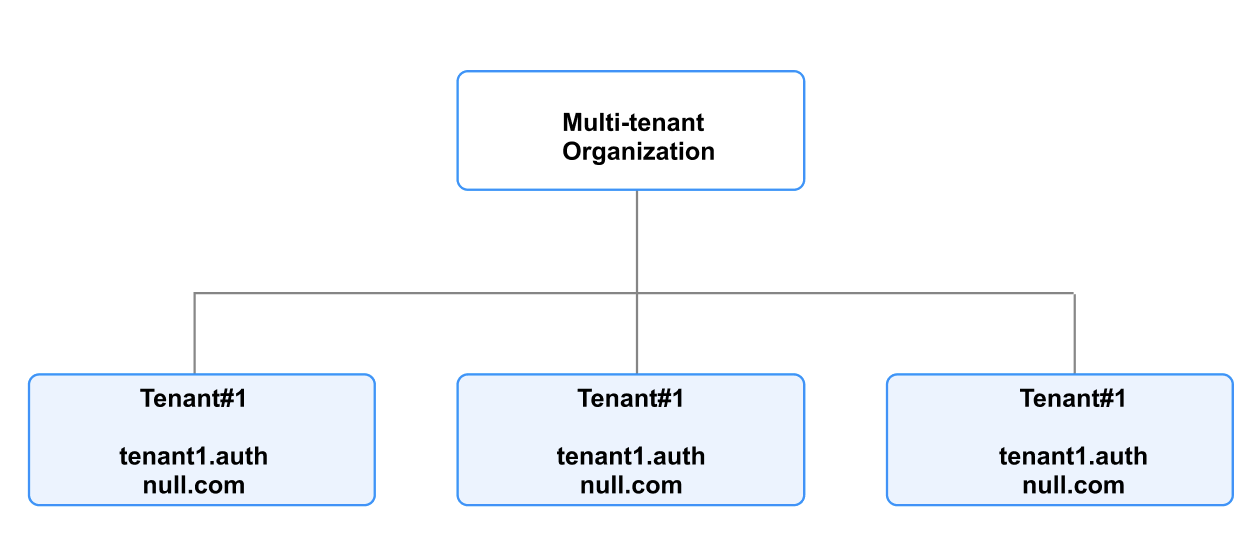
AuthNull’s multi-tenant organization design
AuthNull’s privileged access platform provides for provisioning organizations with multi-tenant built in by design. What I multi-tenancy and why does it matter, and how is the platform organized? T...