Security Automation: How to Automate Incident Response and Threat Mitigation with AuthNull
How to Automate Incident Response and Threat Mitigation with AuthNull
Introduction
As cyber threats grow in complexity and frequency, organizations must move beyond manual security responses. Security automation enables faster and more effective incident response, reducing the impact of cyberattacks. AuthNull is leading the charge in automating security workflows, enhancing detection, and streamlining threat mitigation. In this blog, we explore how security automation can transform incident response and how AuthNull helps organizations achieve a proactive security posture.
The Need for Security Automation
Cyberattacks are evolving rapidly, and traditional security measures struggle to keep up. Manual threat response processes are often slow, error-prone, and resource-intensive. Security automation addresses these challenges by:
- Reducing Response Time: Automating security actions helps neutralize threats in real time.
- Minimizing Human Error: AI-driven automation ensures consistency in incident response.
- Enhancing Threat Intelligence: Integrating machine learning improves threat detection accuracy.
- Improving Compliance: Automated reporting and auditing simplify regulatory compliance.
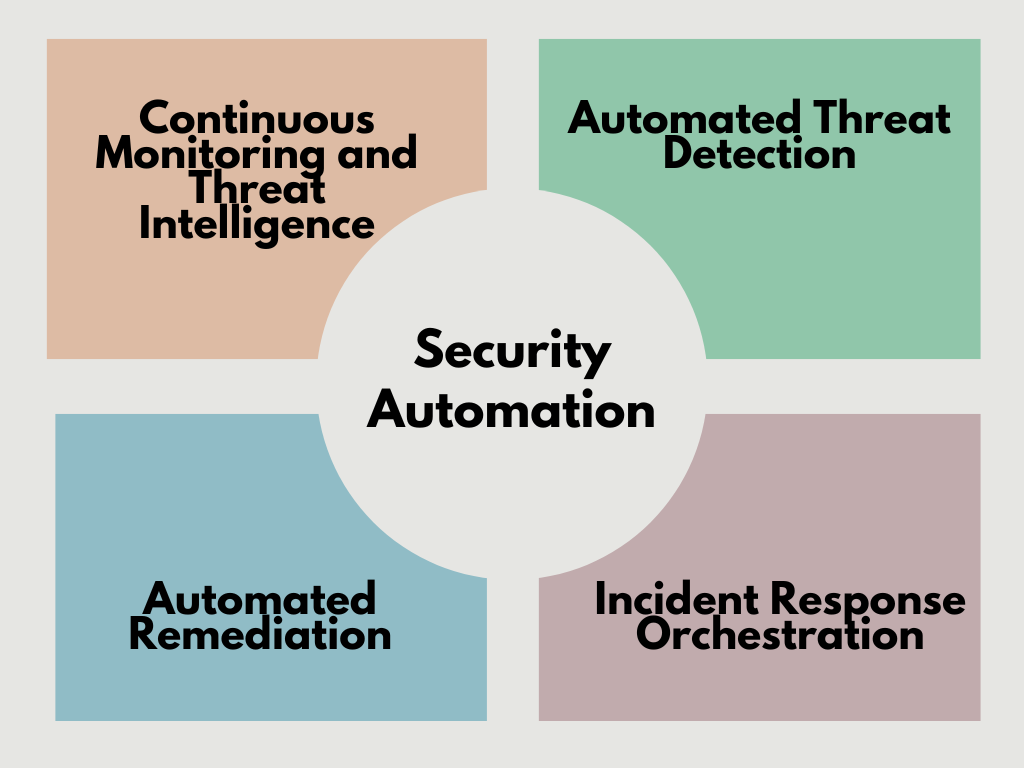
Key Components of Security Automation
1. Automated Threat Detection
By leveraging AI and machine learning, security automation continuously monitors systems for anomalies and suspicious activities, identifying threats before they escalate.
2. Incident Response Orchestration
Security orchestration, automation, and response (SOAR) platforms coordinate workflows, ensuring security teams can respond effectively to cyber threats.
3. Automated Remediation
Automated security controls can contain and neutralize threats without human intervention, reducing the attack surface.
4. Continuous Monitoring and Threat Intelligence
Real-time monitoring and integration with global threat intelligence sources help organizations stay ahead of emerging threats.
How AuthNull is Revolutionizing Security Automation
AuthNull provides cutting-edge security automation solutions to streamline threat detection and incident response. Key features include:
- Agentless Security Operations: Reduce dependencies on traditional endpoint agents while maintaining robust security.
- Privileged Access Management (PAM) Integration: Automate access controls to prevent unauthorized access.
- Zero-Trust Architecture: Implement adaptive access control to ensure only verified identities gain entry.
- AI-Driven Incident Response: Utilize machine learning to predict, detect, and mitigate security threats automatically.
- Real-Time Policy Enforcement: Ensure security policies are dynamically enforced based on risk levels.
Implementing Security Automation with AuthNull
Organizations can integrate AuthNull into their security stack by following these steps:
- Assess Security Gaps: Identify areas where automation can enhance security efficiency.
- Deploy AuthNull’s Security Automation Tools: Implement AI-driven threat detection and response workflows.
- Integrate with Existing Security Systems: Connect AuthNull with SIEM, IAM, and other cybersecurity tools.
- Continuously Optimize Security Policies: Leverage AuthNull’s analytics to refine security measures over time.
Conclusion
Security automation is no longer a luxury but a necessity for organizations looking to stay ahead of cyber threats. AuthNull empowers businesses to automate their security infrastructure, reduce response times, and mitigate threats proactively. By adopting security automation, organizations can achieve a more resilient and efficient cybersecurity posture.