Mastering Endpoint User Management with AuthNull PAM
Mastering Endpoint User Management with AuthNull PAM
In today’s complex IT environments, managing user access across multiple endpoints isn’t just about creating accounts—it’s about building a secure, flexible, and efficient system that works at scale. Whether you’re managing hundreds of servers or thousands of workstations, AuthNull PAM offers a robust solution that combines centralized control with local flexibility.
Think of it like managing a modern office building where you need both sophisticated central security and the ability to handle floor-level access in emergencies. AuthNull PAM brings this dual-layer approach to endpoint user management, allowing organizations to maintain strict security standards while remaining agile in day-to-day operations.
In this guide, we’ll walk through everything you need to know about endpoint user management in AuthNull PAM—from creating users through the admin console to handling emergency access at the endpoint level. Whether you’re new to privileged access management or looking to optimize your existing setup, you’ll find practical insights and real-world examples to help you implement effective user management strategies.
Understanding AuthNull’s Architecture
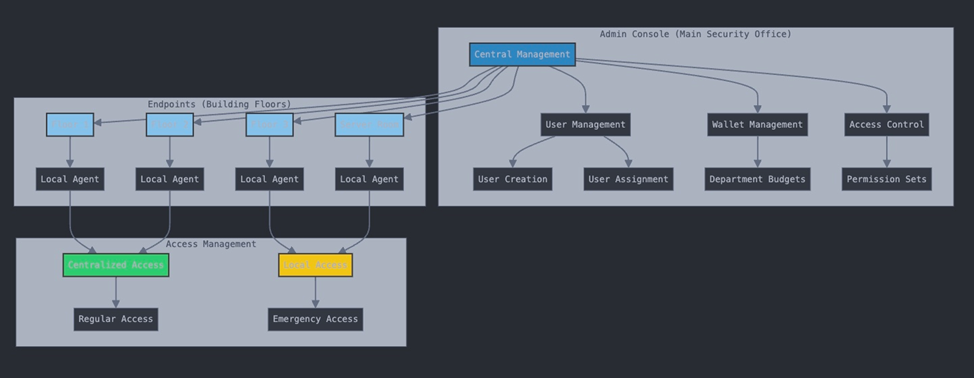 Before diving into user creation, it’s important to understand that AuthNull operates through a dual-layer approach. The system maintains a central management plane (Admin Console) while deploying agents on endpoints to handle local user management. This architecture enables both centralized control and local flexibility when needed.
Before diving into user creation, it’s important to understand that AuthNull operates through a dual-layer approach. The system maintains a central management plane (Admin Console) while deploying agents on endpoints to handle local user management. This architecture enables both centralized control and local flexibility when needed.
Creating Users Through the Admin Console
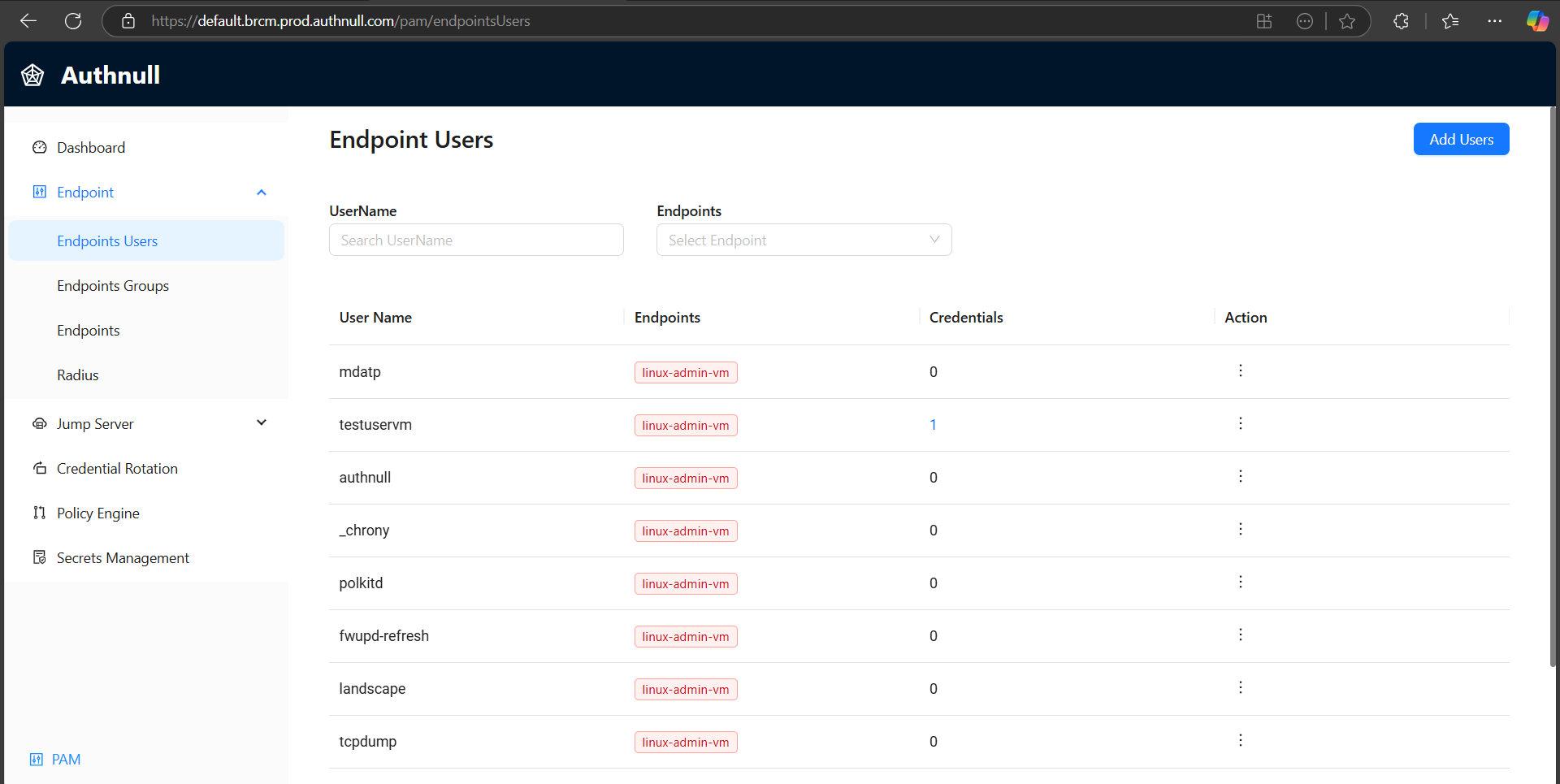
The Admin Console provides a streamlined approach to user management. Here’s how to create a new endpoint user:
1. Navigate to PAM → Endpoint Users → Click “Add User”
2. Fill in the required details:
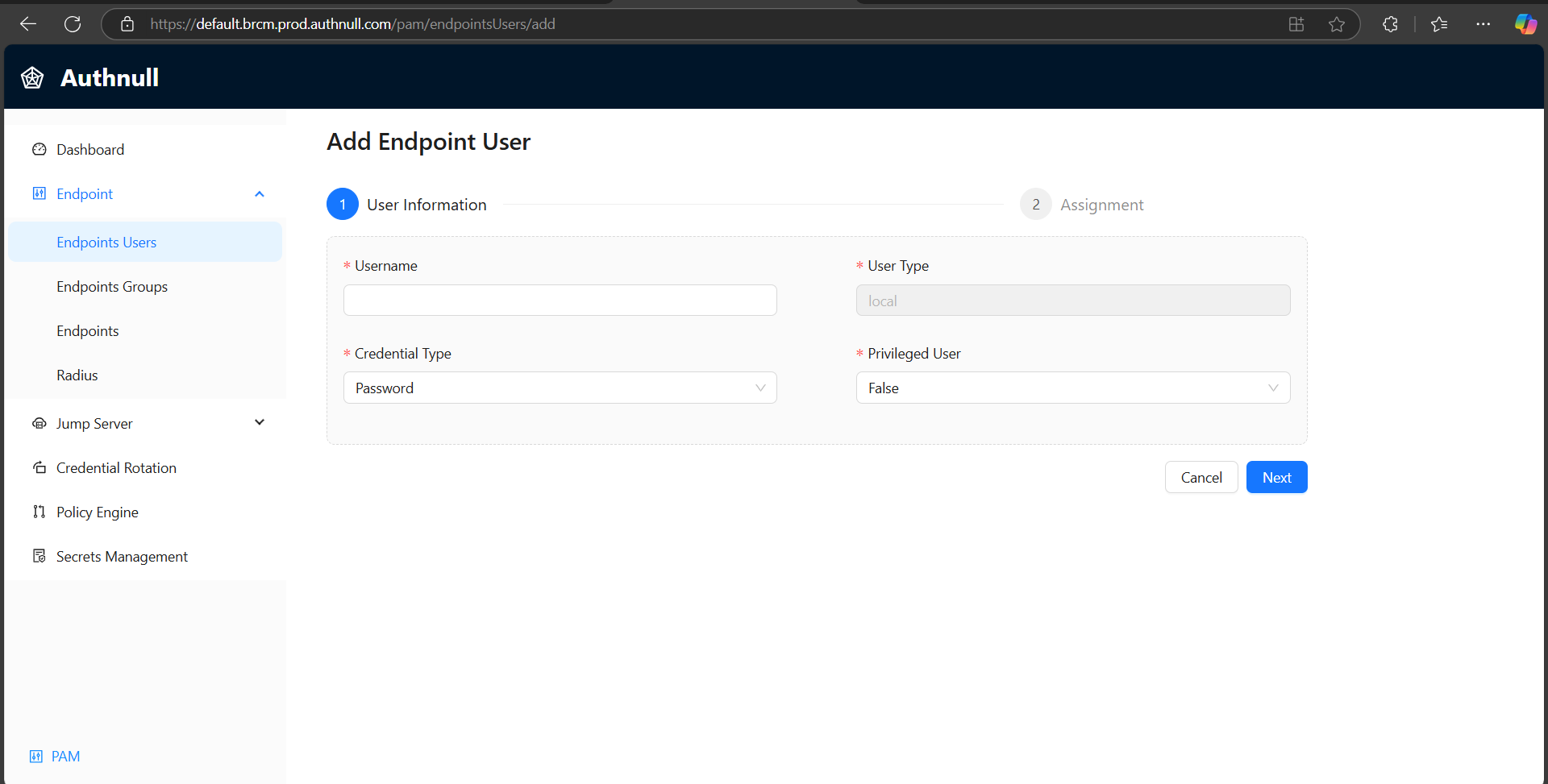
- Username
- Credential Type
- User Type (Privileged/Non-Privileged)
3. In the Assignment section, you’ll need to:
- Select target endpoints
- Configure POSIX groups
- Assign user wallets
- Choose appropriate issuer (e.g., R&D, GTO)
The system will then automatically create local users on the selected endpoints through the deployed agents.
Direct Endpoint User Creation
Sometimes you may need to create users directly on endpoints. While this approach offers flexibility, it should be used judiciously as it temporarily bypasses centralized control:
-
Log in with root/sudo privileges
-
Use the useradd command to create the user:
1
2
3
useradd [OPTIONS] USERNAME
- Set a strong password:
1
2
3
sudo passwd username
The AuthNull agent will detect these changes and synchronize them back to the central console, allowing for subsequent management through the Admin Console.
Managing User Access
After creation, you can manage user access through the Admin Console:
- Navigate to “Endpoint Users” under PAM
- Select users to modify
- Use the Edit function to adjust endpoint assignments
- Verify changes in Endpoint Details
Practical Example
Let’s say you’re onboarding a new IT technician, John:
1.Through Main Security (Admin Console):
- Create John’s ID card
- Grant access to server rooms on floors 2, 4, and 6
- Link his card to IT department budget
- Set working hours access only
2.Emergency Situation:
- John needs urgent weekend access to floor 8
- Floor 8 manager can grant temporary access
- Main security will review on Monday
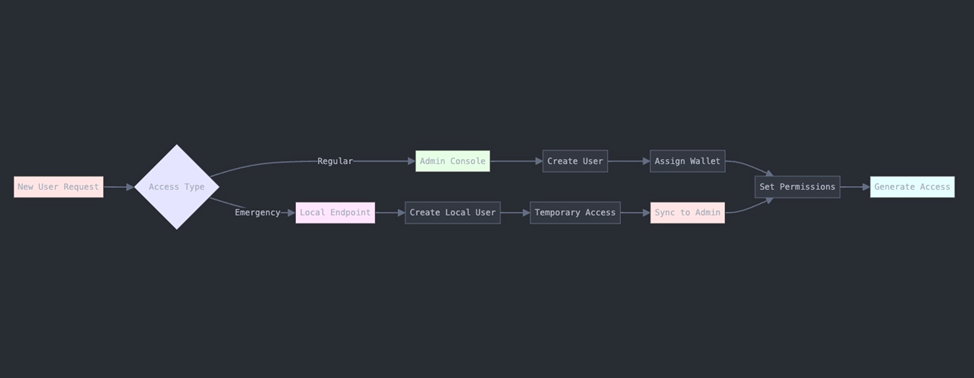
Why This Matters
Just like you wouldn’t want cleaning staff accessing server rooms or marketing accessing payroll offices, AuthNull helps ensure:
- Right people have right access
- All access is tracked
- Emergency access is possible but controlled
- Departments manage their own access budgets
- Central security maintains overall control
This system ensures security while remaining flexible enough for real-world situations - just like a well-managed building’s security system.
Conclusion
AuthNull’s flexible approach to user management allows organizations to maintain both centralized control and local flexibility. By understanding both approaches and following security best practices, you can implement robust privileged access management in your environment.