Privileged MFA
Introducing AuthNull’s latest features, empowering you to manage privileged Multi-Factor Authentication (MFA) based on your organization’s unique security posture and enabling frictionless logins.
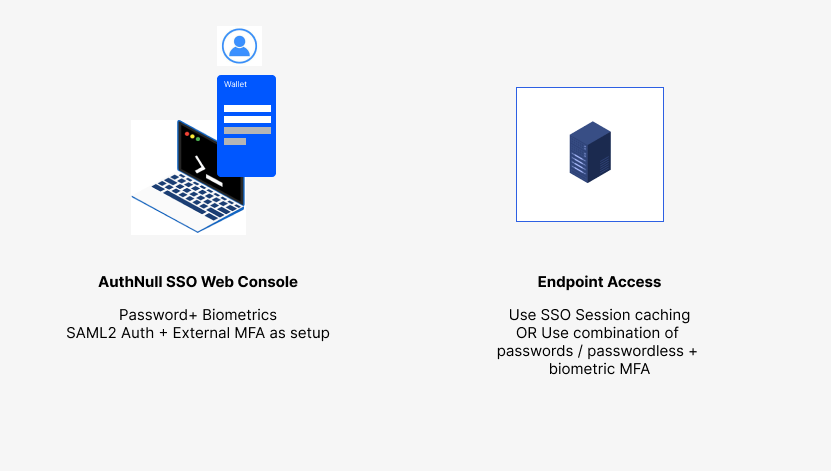
MFA Settings based on the security posture
The initial step involves determining the security posture essential for your organization.If a stringent identity verification is mandated, it is advisable to activate MFA across all facets, including Single Sign-On (SSO) Login and Endpoint access.
Conversely, if the requirement is to validate credentials only once, a single SSO MFA can be employed to streamline the login process for endpoints.
Global Tenant MFA settings are now available

AuthNull’s MFA Wallet & the tenant level MFA device setup
The tenant config supports a MFA Device selection which now defaults to decentralized identity wallet that AuthNull provides. We plan to support other MFA devices soon. However in order to verify identity we always recommend using the AuthNull Wallet.
AuthNull’s wallet uses identtiy verification using biometrics, uses a public / private key pair tied uniquely to the users and acts as an MFA device, authenticator app and a passwords / secrets store.
MFA for SSO console
In the Tenant config screen, when SSO Login MFA for Web Console is setup. If configured with SAMl2, AuthNull seamlessly integrates with the Identity Provider’s MFA. For instance, OKTA users may utilize the OKTA app, while Google users can employ an OTP app.
Please note that while using external apps or MFA, AuthNull cannot guarantee identity verification while accessing admin console. Opting for AuthNull means leveraging its dedicated MFA App and ensuring that every single user identity is verified.
Using SSO Login MFA caching for endpoint access to reduce MFA fatigue
Endpoint Authentication MFA This feature facilitates MFA during every endpoint authentication. Organizations may choose to disable this option to mitigate MFA fatigue, opting instead for MFA caching from the SSO console.
By deactivating endpoint MFA, users can authenticate through a single MFA at the SSO console, employing the same credentials to verify their identity when logging into endpoints.
It’s crucial to note that for such logins, the AuthNull wallet remains a prerequisite, automatically or manually acquiring credentials (passwords, SSH Keys, or passwordless credentials) based on the login type—whether through a jump server or via SSH/RDP connections.
Logging in with AuthNull MFA enabled
When AuthNull MFA is enabled for privileged access authentication on endpoints, AuthNull will require the wallet and will verify the identity of the user through biometrics, verify the credentials - passwords, passwordless and SSH keys. Only after all of these verifications, will the user be allowed to login to the platform.
Service account MFA
Service account MFA forces MFA logins even for M2M authentication as a second step in verifying M2M transactions. Enable it only if you want to force MFA authentication during M2M authentication.
Delivering a frictionless login while enabling biometric MFA during endpoint authentication
When MFA is enabled, additional friction is certain. If so, AuthNull’s wallet can help deliver a fully frictionless authentication experience while enabling a biometric MFA.
Demo below:





