Entra Id Windows logon — with phishing‑resistant MFA, Just‑in‑Time privilege and policy‑based Conditional Access
Today we’re releasing AuthNull Windows Agent v3.0 with native Microsoft Entra ID integration.
Until now the agent has protected classic on‑prem Active Directory (AD) logons; from this version forward it can also enforce our cloud MFA and Zero‑Standing‑Privilege controls on Entra‑joined or hybrid‑joined Windows 10/11 endpoints—all before the user ever reaches a desktop.
Why this matters
-
Desktop sign‑in is still single‑factor for most organisations. Windows Hello or FIDO2 keys are great but require modern hardware, Intune policy and user enrolment campaigns — hurdles that keep many firms on passwords alone.
-
Conditional Access stops after logon. Microsoft CA evaluates risk only once the primary credential succeeds; a stolen password still gives an attacker a local session token. Premium P1 (or P2 for risk‑based policies) is also a hard licence ceiling for many estates.
-
External Authentication Method (EAM) is still new. A handful of MFA providers have registered with the Entra EAM API, but none extend the same factor down to privileged desktop actions or Unix/DB sessions. EAM support will be separately added soon.
Prerequisites
An active Entra ID P1 will be required for this functinality, in addition Microsoft may require other Entra ID licenses.
What we built
Credential Provider plug‑in
Replaces Winlogon password prompt with AuthNull’s passkey / push / biometric challenge—works for Entra‑joined, hybrid‑joined and AD‑joined devices.
Policy based access control built in
Evaluates AuthNull Conditional Access rules (geo, device posture, user risk) offline if the endpoint is temporarily disconnected.
How does it work?
Users will need to sign up with Entra id, create an app. Then use that client id and secret to configure Entra ID on AuthNull.
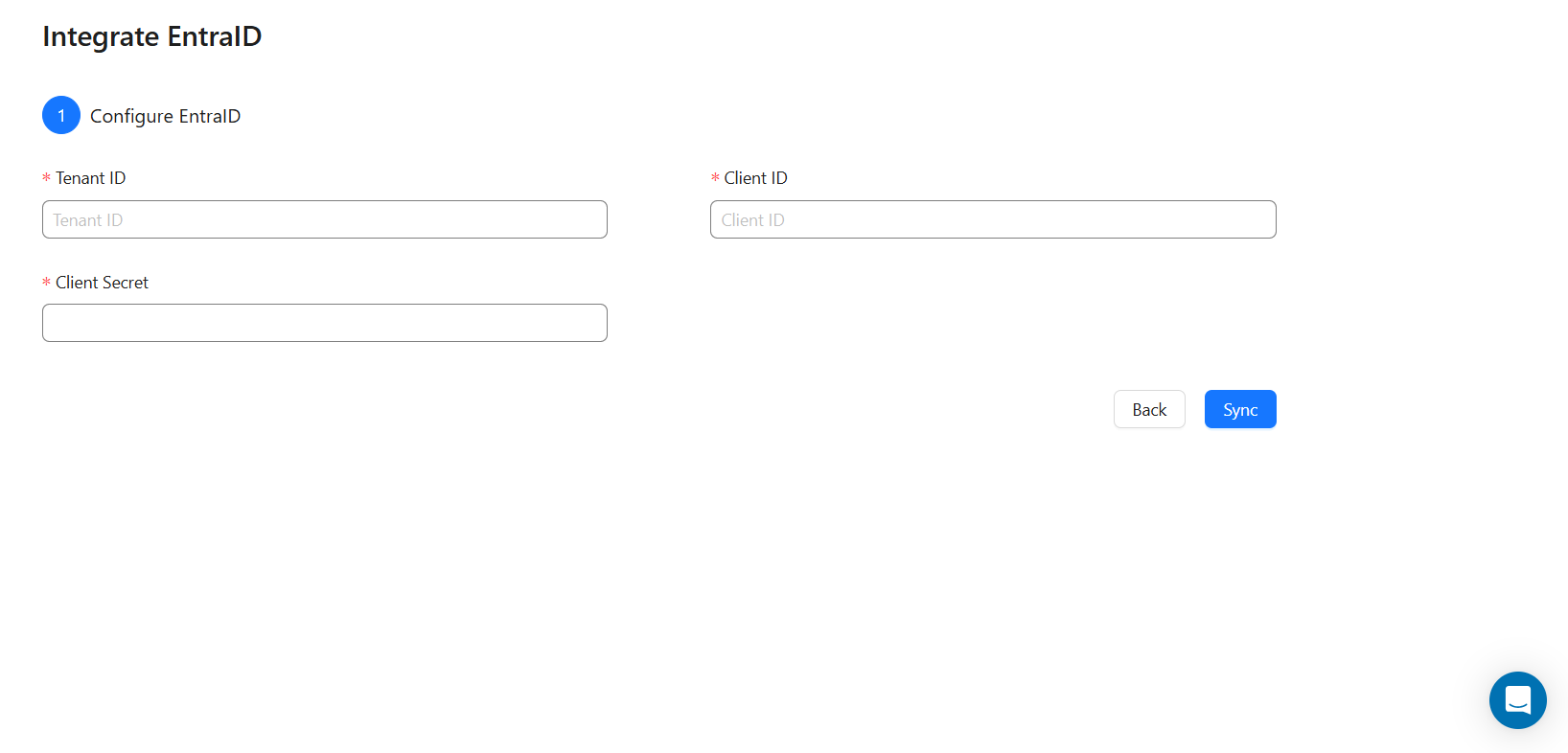
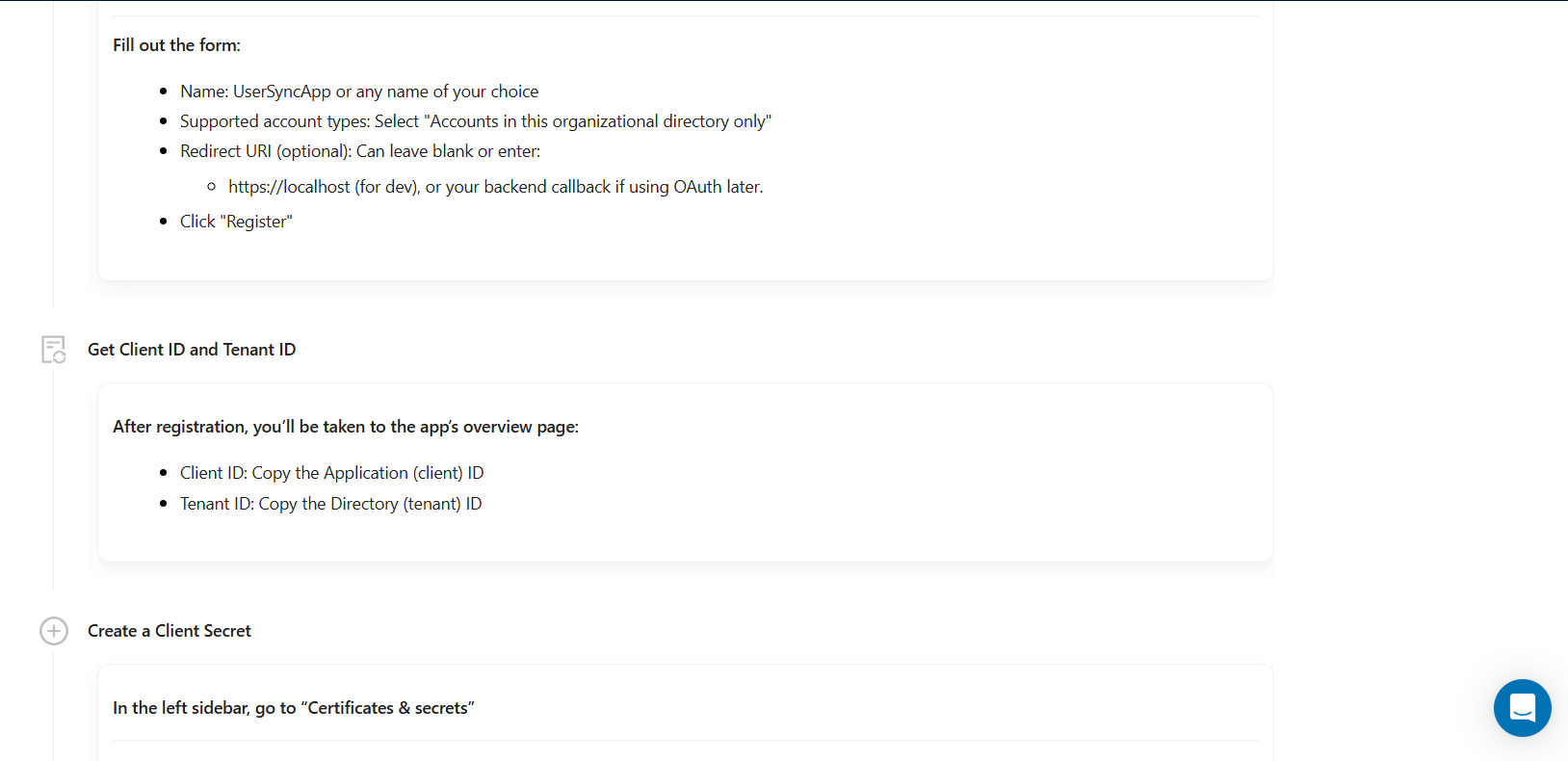
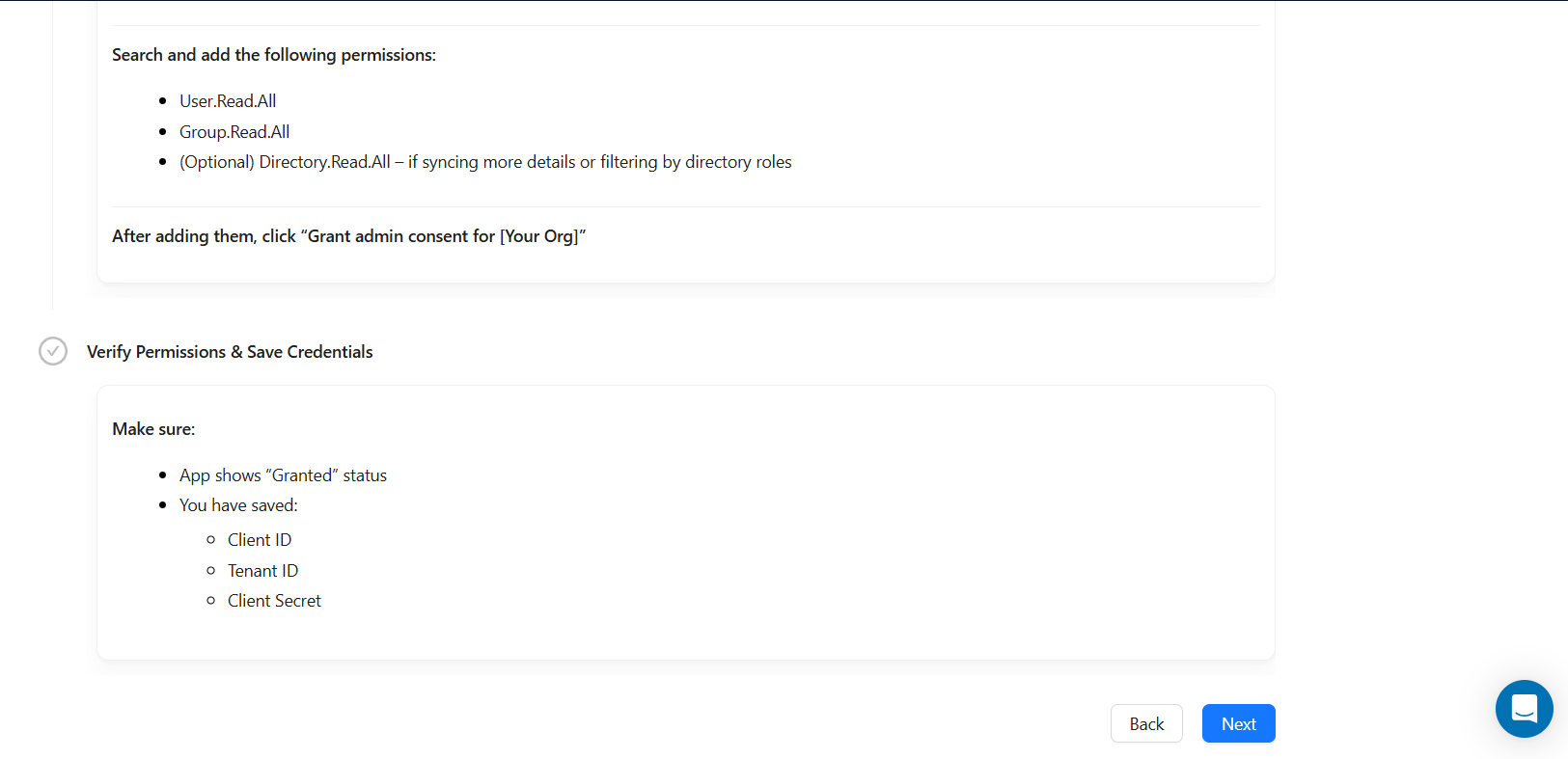
Configuring windows endpoints to connect to Entra ID
Once this is done, administrators need to install AuthNull’s agents on to all windows machines and configure the credential provider to connect to their respective domains on Entra id.
How it works — authentication flow
-
User hits Ctrl‑Alt‑Del → AuthNull credential provider renders QR/passkey/biometric prompt.
-
AuthNull Cloud verifies the credentials provided (against Entra ID) and the second factor.
-
AuthNull evaluates Conditional‑Access policy; deny, allow, or step‑up (second factor, device check, Geo‑IP) decision is made offline.
-
AuthNull allows the user to logon locally with the Entra ID provided credentials.
Roadmap
External Authenticator Method for AuthNull is coming. This will add support for Windows Web logons, and application logons against Entra id, enabling AuthNull MFA and Conditional access.





