Automated Policy Generation
Introductions
AuthNull has a new feature of automated policy generation now. This feature does the following automated policy generation for all types of policies that we can discover without human intervention required to create fine grained access policies.
How does this work? And what does this work against?
This works against all infrastructure we protect – Radius, Active Directory, Endpoints, Service Accounts etc.
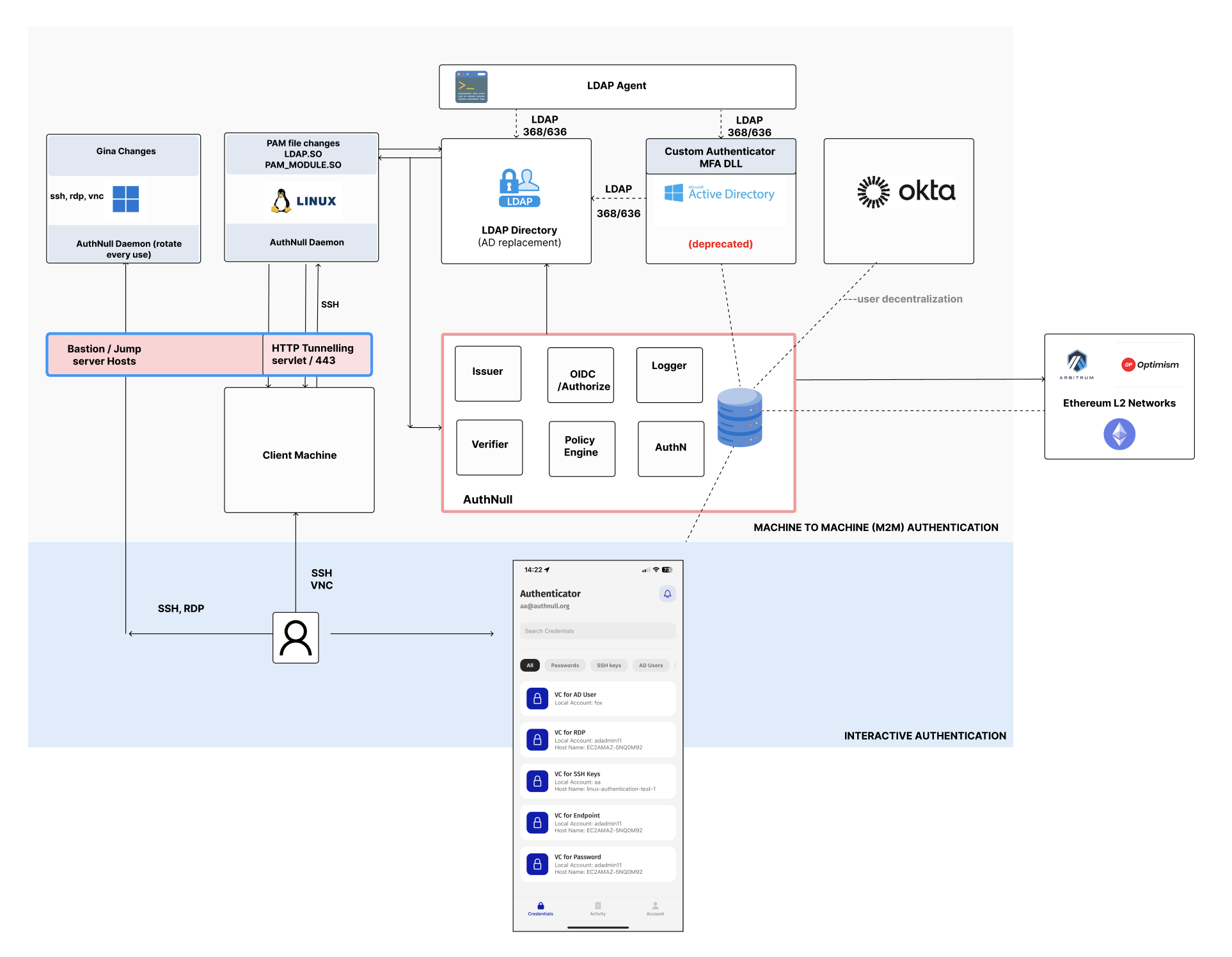
Shown in the diagram we have Active Directory bridge / Agent, Radius Bridge or the agent, Endpoint Agents and the AuthNull’s infrastructure we do.
The system is designed in a way that all the authentication logs happening is streamed to a Logging Service which then generates Automatic Policies out of the Logs received.
– Audit logging – log all auth requests – Policy generation automatic generation of policies for Active Directory bridge / Agent, Radius Bridge or the agent, Endpoint Agents – Policy enforcement of policies generated.
Here’s how it works:
Step #1 These are the list of policies which can be generated via this new feature.
Step #2: List of all the Automatically Created Policies
These Policies are automatically Generated when the User tries Authentication to the Respective System ( AD / Radius / Service Account / Endpoint), The Logs are fetched, and it is Generated as a Policy and thus made available in the system.
An overview of the various kinds of policies
RADIUS Policy:
Network access control must enforce strong authentication. Configure RADIUS to require certificates alongside credentials, implement automatic session termination, and maintain detailed access logs. Critical: Enable accounting to track all authentication attempts and enforce role-based access control (RBAC) through vendor-specific attributes.
Active Directory Policy:
AD requires rigorous hygiene. Implement fine-grained password policies with complexity requirements and regular rotation. Crucial but often overlooked: Enable Privileged Access Management to control privileged account usage, configure SID filtering for all trusts, and regularly audit Group Policy Objects for unauthorized modifications.
Endpoint Policy:
Defense-in-depth at the endpoint level is vital. Require disk encryption, restrict USB device usage, enforce application whitelisting, and maintain current patch levels. Key insight: Implement behavioral analytics alongside traditional endpoint protection to detect anomalous activity patterns.
Service Account Policy:
Service accounts represent significant risk surface. Implement managed service accounts where possible to handle password rotation automatically. Critical control: Configure Service Principal Name (SPN) registration restrictions and monitor for unauthorized SPN modifications that could enable Kerberos delegation attacks.
FAQs:
What kinds of policies does it generate?
It Generates Endpoint, AD, Radius, Service Account Policies out of Authentication Logs.
Can I edit these policies ? -Yes, you can edit these policies.
How do I disable auto generation?
Can I edit conditional access?
Yes, we can Edit Conditional Access