Frictionless privileged access through automated policy discovery
AuthNull’s Policy Engine is a new feature built to by automatically identifying and creating authentication policies for privileged users. AuthNull’s Policy Engine enables a significant step towards achieving Zero Trust in privileged access without needless friction.
By automating the discovery of authentication policies, AuthNull streamlines the process and bolsters security without introducing friction and delays both in the secops, and in the user experience.
How does this work?
Setting up the tenant to discover policies
The first step in being able to discover authentication requests and policies is to setup the tenant to be able to discover policies.

This is done by enabling the tenant to be in “audit mode”. By doing this, admins can ensure that no authentication requests are denied when AuthNull is being rolled out and AuthNull automatically discovers all authentication requests and policies.
The tenant can be configured to run in these three authentication modes:

Where are the policies discovered from?
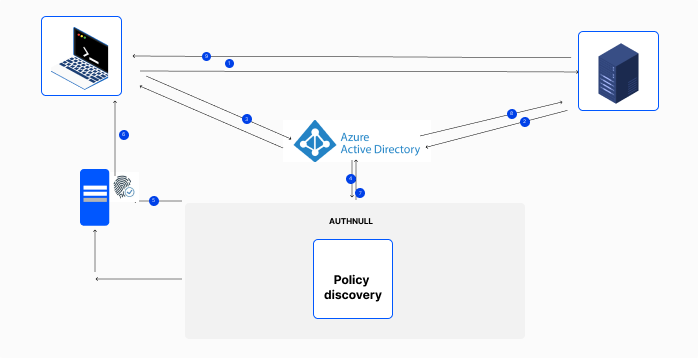
When you configure authentication for endpoints, AuthNull intercepts all authentication requests.
Today we only support discovery of authentiation discovery from Endpoints. In the near future, integration of Active Directory or Azure AD will be supported to discover user auth against those control points.
Setting up Endpoints for policy discovery
To setup endpoints, follow instructions on setting up endpoints from this link
Reviewing requests
When users authenticate, AuthNull intercepts those requests and is able to showcase to the administrators in the requests screen. Subsquently it is easy to review all of these requests and convert them into policies.

Subsequently each of these requests can be reviewed by admin and approved or rejected. By approving, this becomes an acceptable authentication policy that will be allowed to authenticate.

Finding policies that are active for this tenant
Finally, all policies for this tenant can be seen by going to the policies section. All tenant level authentication policies are visible on this screen. Administrators can see / review / edit these policies.
Creating policies explicitly
Policies can also be created explicitly as required where a given directory user, can be given access to one or more endpoints, and if required one or more local users on those endpoints.

Moving to Zero Trust
When admins have put the system through a “audit mode” i.e. a learning mode, discovered, reviewed and approved or rejected various authentication policies, they can then switch on the policy enforcement by changing the tenant to “live mode”.
This will begin enforcing all policies when they are ready.





