Support for Radius MFA with passwordless, and decentralized credentials
Support for MFA and Privileged Access to Radius Devices with Passwordless and Decentralized Credentials.
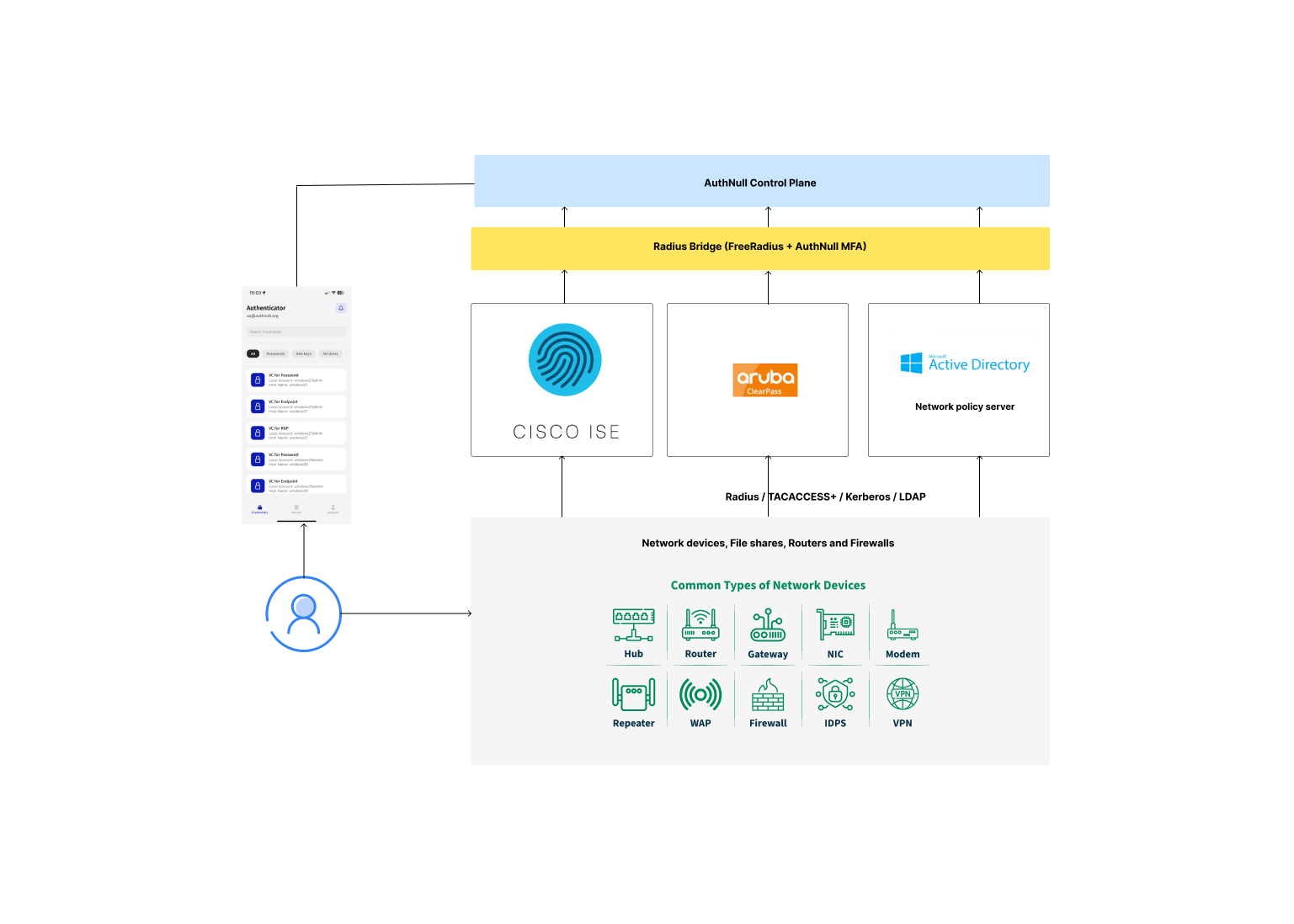
We’re announcing public preview support for Radius Privileged Access and MFA with the use of a FreeRadius based Radius Authentication Bridge (here after referred as a Radius Bridge). Previously Radius MFA was an internal preview available to select customers.
The Radius Bridge by AuthNull enables MFA on radius powered devices.
Specifically, AuthNull announces Radius-based support for enabling network devices to authethenticate to the AAA devices with MFA where the 2nd factor is a passwordless claim.
-
Microsoft NPS
-
FreeRadius
-
Cisco ISE
-
HPE Clearpass
The Role of RADIUS in Authentication
RADIUS acts as a bridge between network services and AAA servers. While it doesn’t define authentication methods itself, it supports various protocols, making it adaptable to different use cases. These include:
-
Extensible Authentication Protocol (EAP): A flexible framework supporting multiple authentication methods, often used with certificates and PKI. EAP encapsulates the authentication process and is commonly employed in wireless networks and VPNs.
-
Password Authentication Protocol (PAP): A straightforward method where credentials are sent in plain text. While simple, it is less secure, relying on shared secrets for basic obfuscation.
-
Challenge-Handshake Authentication Protocol (CHAP): A more secure alternative to PAP, using a challenge-response mechanism and one-way hash functions to ensure passwords are not directly transmitted.
-
MS-CHAP and MS-CHAPv2: Microsoft’s variant of CHAP with stronger cryptography and mutual authentication, making it more secure for modern applications.
Flow of Radius Authentication using AuthNull’s Radius bridge
The RADIUS packet flow demonstrates how this protocol handles authentication requests in conjunction with AuthNull:
-
Access Request: The client device (a network access server, NAS) sends a request containing user credentials and additional attributes to the RADIUS server.
-
Request Processing: The RADIUS server verifies credentials against a user database, often with the help of the AuthNull Authentication Proxy. This might involve Active Directory or another downstream RADIUS server.
-
Challenges (Optional): For challenge-response authentication, the server may send an additional challenge to the client, prompting further user input.
-
Multi-Factor Authentication (MFA): Once the user’s credentials are validated, AuthNull invokes MFA through its cloud service to add another layer of security. Remember that in order to authenticate through AuthNull, you require an AuthNull configured Radius policy that allows the given users to the said resources.
-
Access-Accept or Access-Reject: Based on the results, the server either grants access with specific conditions or denies it entirely.
Throughout this process, RADIUS leverages UDP for communication, with encryption ensured by shared secrets between the client and server.
Radius Matters
Despite being a legacy protocol, RADIUS persists because it is deeply embedded in network ecosystems. Its ability to manage centralized authentication for VPNs, wireless access points, and network appliances makes it irreplaceable in many scenarios. Additionally, platforms like AuthNull enhance RADIUS functionality by adding modern security measures such as MFA. For organizations unable to fully migrate to protocols like SAML or OIDC, RADIUS serves as a reliable bridge.
AuthNull’s Radius bridge for MFA (i.e Radius Bridge)
AuthNull’s radius bridge is essentially a pre-packaged, secure FreeRadius server combined with AuthNull’s MFA modules that call the AuthNull cloud (or your tenant hosted) services to request passwordless MFA.
Why Radius MFA matters?
1. Compliance with Security Frameworks
CIS Controls:
The Center for Internet Security (CIS) emphasizes the importance of strong authentication in its Critical Security Controls, particularly under Control 6 (Access Control Management). MFA implemented through RADIUS ensures compliance by adding a layer of authentication beyond simple passwords, which are often vulnerable to brute force attacks.
NIST Guidelines:
The National Institute of Standards and Technology (NIST) advocates for MFA as part of its Digital Identity Guidelines (SP 800-63B). RADIUS MFA aligns with these recommendations, offering an additional layer of identity proofing, especially in environments where traditional passwords are insufficient. NIST explicitly warns against using single-factor authentication in high-risk scenarios.
2. Executive Orders on Cybersecurity
Executive Order 14028 (Improving the Nation’s Cybersecurity):
This mandate highlights the need for government agencies and contractors to adopt MFA to enhance cybersecurity defenses. RADIUS MFA facilitates compliance with these mandates by providing a method for securing network devices, VPNs, and other critical infrastructure.
Zero Trust Strategy Alignment:
The Executive Order also pushes organizations toward Zero Trust Architecture. RADIUS MFA is integral to this model, as it verifies user identity and device security continuously, ensuring trust is not assumed based on previous interactions.
Enhanced Protection Against Credential-Based Attacks
RADIUS MFA mitigates the risks associated with compromised credentials, which remain a primary attack vector in breaches, as noted in multiple NIST reports and the Verizon Data Breach Investigations Report. By requiring a second factor, RADIUS reduces the effectiveness of stolen credentials.
3. Applicability Across Diverse Environments
Broad Adoption:
Many network devices and services, from VPNs to wireless access points, rely on RADIUS for authentication. Adding MFA through RADIUS ensures these critical systems are secured without requiring a complete overhaul of legacy infrastructure.
Interoperability:
RADIUS MFA supports various authentication mechanisms, allowing organizations to integrate modern security practices with legacy systems, ensuring compliance while maintaining operational continuity.
Scalability and Centralized Management
Organizations can manage MFA centrally through RADIUS, enabling scalable deployment of MFA policies across diverse environments. This approach supports CIS recommendations for centralizing authentication management to reduce misconfigurations and security gaps.
4.Regulatory Requirements and Industry Standards
HIPAA and PCI DSS:
Regulatory frameworks like HIPAA for healthcare and PCI DSS for payment systems mandate strong access controls. RADIUS MFA helps meet these requirements by ensuring that only authenticated, authorized users can access sensitive systems.
Critical Infrastructure Protection (CIP):
In sectors like energy and transportation, RADIUS MFA addresses the need for securing critical systems, as outlined in NERC CIP standards and federal cybersecurity recommendations.
5. Future-Proof Security Posture
While modern protocols like SAML or OIDC are becoming prevalent, RADIUS MFA bridges the gap for legacy systems. This ensures compliance with mandates while organizations gradually transition to advanced authentication frameworks, maintaining a robust security posture in the interim.
By aligning with mandates from CIS, NIST, and Executive Orders, RADIUS MFA not only enhances security but also ensures compliance with critical regulatory and security standards, making it an essential component of any robust cybersecurity strategy.
AuthNull’s Radius Bridge uses Decentralized for MFA
AuthNull’s Radius MFA is powered by Decentralized identity based credentials (using Verified credentials). Verified credentials help users retain ownership of data (like passwords) which are not stored on a central password store, and instead directly transmitted to the user device. Additionally the 2nd factor which is a passwordless credential is a claim, signed by the users’s private key enabling easy and secure access.





