Conditional Access for on-prem Active Directory
AuthNull provides native support for conditional access to on-prem Active Directory. This means that any identity that is used on Windows or Linux machine that is joined to the domain and authenticates against active directory can be used for conditional access.
What can you control access to on an on premise Active Directory?
An Identity can be assigned access to another user, service account, or groups. Additionally access can be provided to a set of machines based on conditions.
Conditional Access for Linux
Provide conditional access to Linux hosts based on User Behavioral Analytics (UBA), User Risk, Session Risk variables
Add / remove local entitlements
AuthNull can add / remove local entitlements to Linux hosts based on various conditions.
Users can dynamically be added to sudoers
AuthNull can add / remove users from sudoers, and enable them to run specific commands based on various conditions.
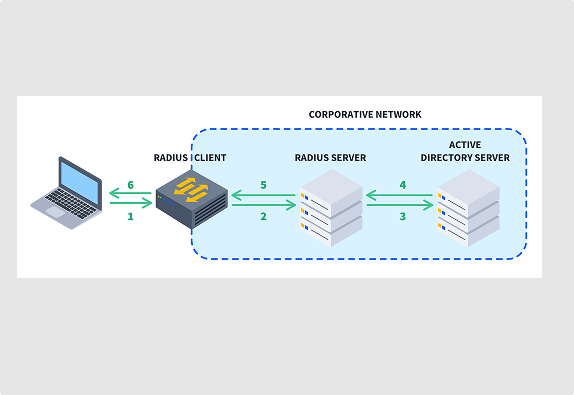
Conditional Access for Radius Devices
AuthNull can provide conditional access to Radius based on a variety of condititions.
Access to specific Radius devices
AuthNull can provide access to specific Radius devices based on various conditions.
What kinds of Radius Infrastructure is supported?
We support all Radius Infrastructure including Microsoft NPS / Radius, FreeRADIUS, Cisco ISE and Clearpass.
Conditional access for privileged local users on Windows
You can control access to Windows hosts and local users using conditional access policies.
What can be controlled
Groups that the local user is a member of, and the local user's local entitlements.

Condittional Access for Open Source Databases
AuthNull can provide conditional access to databases.
Supports open source databases
Supports open source databases like PostgreSQL, MySQL, and MariaDB.PostgreSQL, MySQL, and MariaDB
What features are supported for databases?
All conditional access controls are supported including location, network, device, user and session risk, timebound, and just in time access.

Conditional Access Controls: What's available
Location, Network and Device
Enables targeting of users based on location, network and device.
How is this used?
AuthNull continously tracks the user location, network and device and uses that to check specific policy conditions so as to enable conditional access.
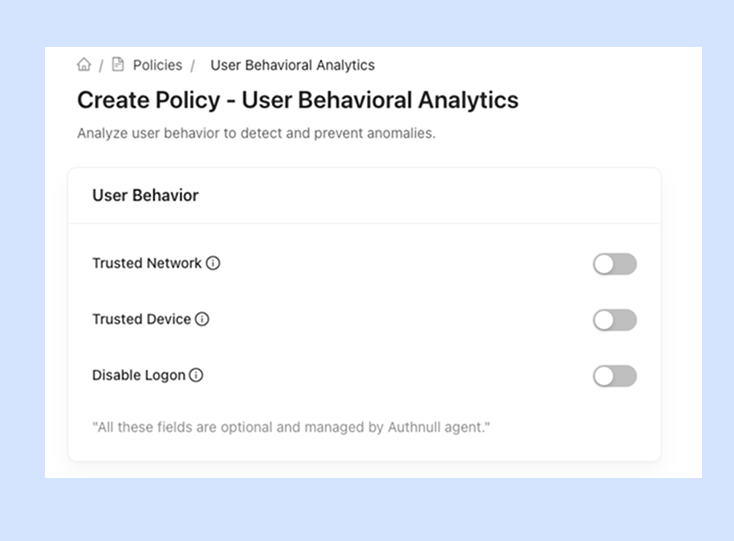
User Behavioral Analytics
Provide conditional access to Linux hosts based on User Behavioral Analytics (UBA), User Risk, Session Risk variables
Trusted Network, Devices and Locations
AuthNull can track the user's network, device and location and establish trusted baselines.
Organizations can change the UBA baselines
Organizations can change the UBA baselines based on their risk tolerance.
Identity and Session Risk
AuthNull enable targeting based on user and session risk
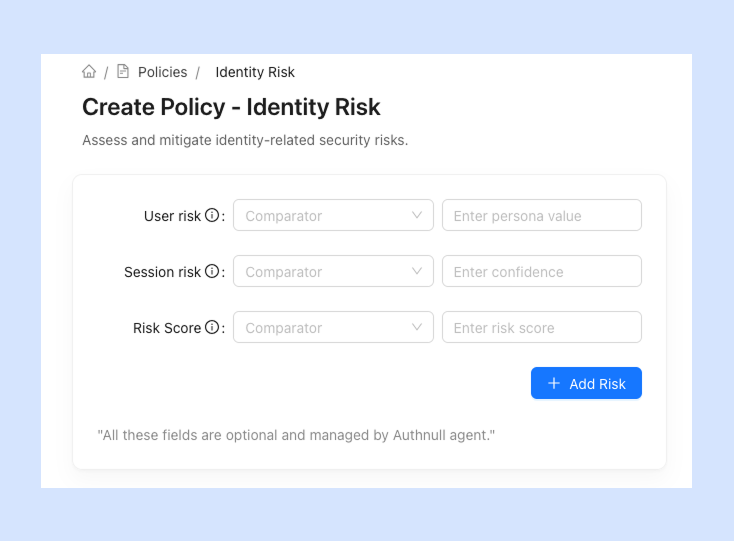
Create policies targeting Identity and Session Risk
Enables conditional access based on user identity and session risk.
What kinds of controls are supported?
User risk - a unique risk score for each user based on the user's risk factors, over time. Organizations can adjust this risk score or view them for each user.Session risk - a unique risk score for each session based on the session's risk factors, over time. This risk score is unique for each session.
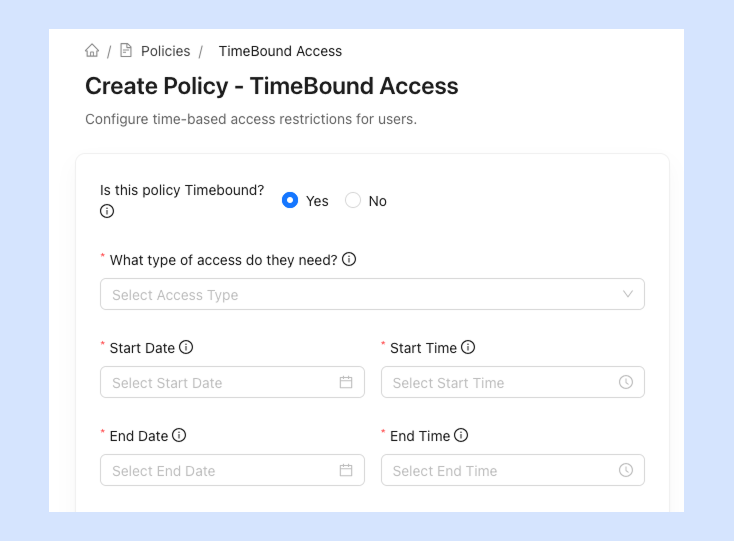
Time Bound Access
Enables conditional access based on user identity and session risk.
What kind of controls are supported?
Create policies that deliver access on a specific data time, for one time or recurring basis.
Just in Time Access
AuthNull can provide just in time access to resources for true Zero Standing Privileges..
How does this work for legacy infrastructure such as Active Directory
For legacy infrastructure such as Active Directory, AuthNull's just in time policies work the same way as the timebound policies.

Compare Conditional Access
|
Azure Conditional Access
|
AuthNull
|
|
|---|---|---|
| Active Directory on prem | Yes. But requires intune, and Entra P1 license. | Yes. Natively supported with Agentless and Agent based setup. |
| Radius Conditional access | Natively supported | Natively supported |
| Database Conditional Access | Not supported | Supported for Postgres, MySQL and MariaDB |
| Entra ID as the identity store | Supported Natively | Support available soon |
| Linux support for Conditional Access | Not supported | Native support with Database specific policies |
| Starting cost |
$$
$10+ per user per month
|
$
$6 per user per month
|
Entra id is trademark of Microsoft corporation. AuthNull is not affiliated with Microsoft corporation and this information is not endorsed by Microsoft corporation.