Decentralized Identity: The Future of Identity Management for the Federal Government
The federal government is facing a number of challenges in the area of identity management. Current systems are often fragmented, outdated, and insecure. This makes it difficult for the government to verify the identities of its citizens, which can lead to fraud, security breaches, and other problems.
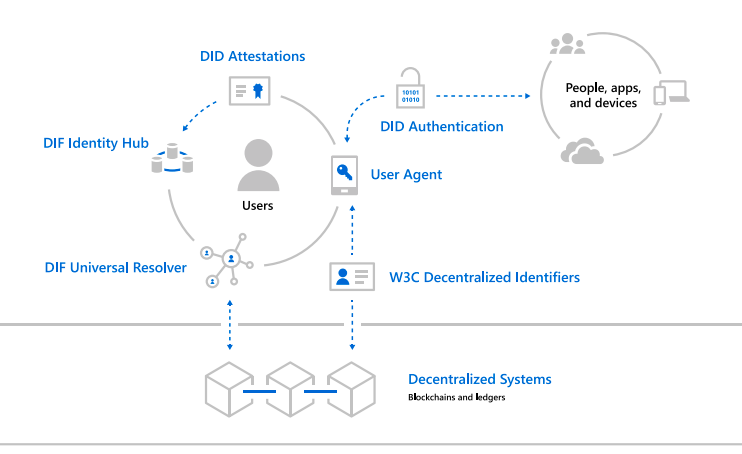
Decentralized identity (DID) is a new technology that has the potential to address these challenges. DIDs are a way of storing and managing identity information in a secure and decentralized way. This means that the government would no longer need to rely on centralized systems to verify the identities of its citizens.
DIDs are based on a set of standards that define how identity information is stored and managed. These standards are designed to be interoperable, so that DIDs can be used across different systems and applications.
A DID consists of a unique identifier, a public key, and a set of claims. The identifier is used to uniquely identify a DID, while the public key is used to verify signatures. The claims are a set of statements about the DID, such as the name of the individual or organization associated with the DID.
DIDs are stored in a distributed ledger, such as a blockchain. This means that the identity information is not stored in a central database, which makes it more secure.
How can DID be used by the federal government?
DIDs could be used by the federal government to improve the way it manages identity in a number of ways, including:
-
Streamlining the process of verifying identities for government services: DIDs could be used to create a single, decentralized identity that could be used to access all government services. This would eliminate the need for individuals to create separate accounts and passwords for each government service, which would make it easier and more secure to access government services.
-
Reducing the risk of fraud and identity theft: DIDs could be used to create a more secure way to verify identities. This is because DIDs are stored in a distributed ledger, which makes them more difficult to hack or tamper with. Additionally, DIDs could be used to create a more dynamic way to verify identities. For example, a DID could be used to verify an individual’s identity for a specific purpose, such as applying for a loan or voting. This would make it more difficult for criminals to use stolen identities to commit fraud.
-
Improving the privacy of individuals’ identity information: DIDs could be used to give individuals more control over their identity information. This is because individuals would be able to choose which organizations and applications have access to their DID. Additionally, DIDs could be used to encrypt identity information, which would make it more difficult for unauthorized individuals to access it.
-
Making it easier for individuals to access government services from anywhere in the world: DIDs could be used to create a more globalized way to access government services. This is because DIDs are not tied to a particular country or region. Additionally, DIDs could be used to create a more seamless way to transfer identity information between different countries. This would make it easier for individuals to access government services from anywhere in the world.
How can DID be used by the federal government for PAM solutions?
DIDs could also be used by the federal government for PAM solutions. PAM solutions are used to manage privileged access to sensitive systems and data. By using DIDs, the federal government could improve the security of its PAM solutions in a number of ways, including:
-
Streamlining the process of granting and revoking privileged access: DIDs could be used to create a single, decentralized identity that could be used to grant and revoke privileged access to all government systems. This would eliminate the need for organizations to manage separate accounts and passwords for each system, which would make it easier and more secure to manage privileged access.
-
Reducing the risk of unauthorized access to privileged accounts: DIDs could be used to create a more secure way to grant and revoke privileged access. This is because DIDs are stored in a distributed ledger, which makes them more difficult to hack or tamper with. Additionally, DIDs could be used to create a more dynamic way to grant and revoke privileged access. For example, a DID could be used to grant privileged access for a specific task, such as patching a system or installing software. This would make it more difficult for unauthorized individuals to gain access to privileged accounts.
-
Improving the visibility of privileged access: DIDs could be used to provide organizations with more visibility into who has access to privileged accounts and what they are doing with those accounts. This would help organizations to identify and mitigate risks associated with privileged access.
-
Making it easier to comply with regulations: DIDs could be used to help organizations comply with regulations that govern privileged access. For example, DIDs could be used to track and audit privileged access activity, which would help organizations to demonstrate compliance with regulations such as PCI DSS and HIPAA.
Conclusion
DIDs have the potential to revolutionize the way the federal government manages identity and privileged access. By adopting DIDs, the government can improve privacy, security, efficiency, and transparency.
Additional information about DIDs
DIDs are still a relatively new technology, but there are a number of projects underway to develop standards and regulations for DIDs. The W3C Decentralized Identifiers (DID) Working Group is developing a set of standards for DIDs. The Sovrin Foundation is a non-profit organization that is developing a global DID network.
How can you benifit from DIDs?
We at AuthNull are dedicated towards building a PAM solution that allows your organization to control your decentralized identity. Connect with us and learn how you can adopt the passwordless solution for your critical IT infrastructure.