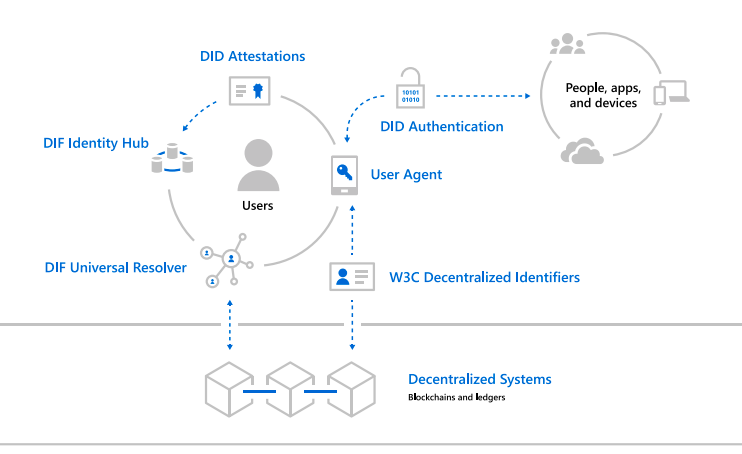
Why decentralized identity for implementing passwordless authentication?
Decentralized identity is the best option to implement passwordless authentication for the following reasons:
Two roots of trust
All authentication is done by two roots of trust, and using FIPS compliant public key cryptography on both sides. All credentials require cryptographic signatures of both the Issuer (organization) and holder (end user).
Credentials are issued by organization, and decentralized.
All credentials are issued by the organization, and sent to the user's wallet where the user signs with their private key and stores it in the wallet.
Standards Based
All credentials are issued as W3C verified credentials in compliance with NIST special publication 800-63-3.
No single, central attack surface
All credentials are completely decentralized. No local privileged accounts can be accessed without a decentralized credential.
Tamper evident credentials
All credentials and identities are tamper evident as identities and credential transaction hashes can be written to blockchain as merkle hashes. When modified, this alters the address on the blockchain indicating compromise. AuthNull comes with extensive logging and audit checking capabilities to prove tampering.