Next Generation EPM
Manage thousands of Endpoints with Ease
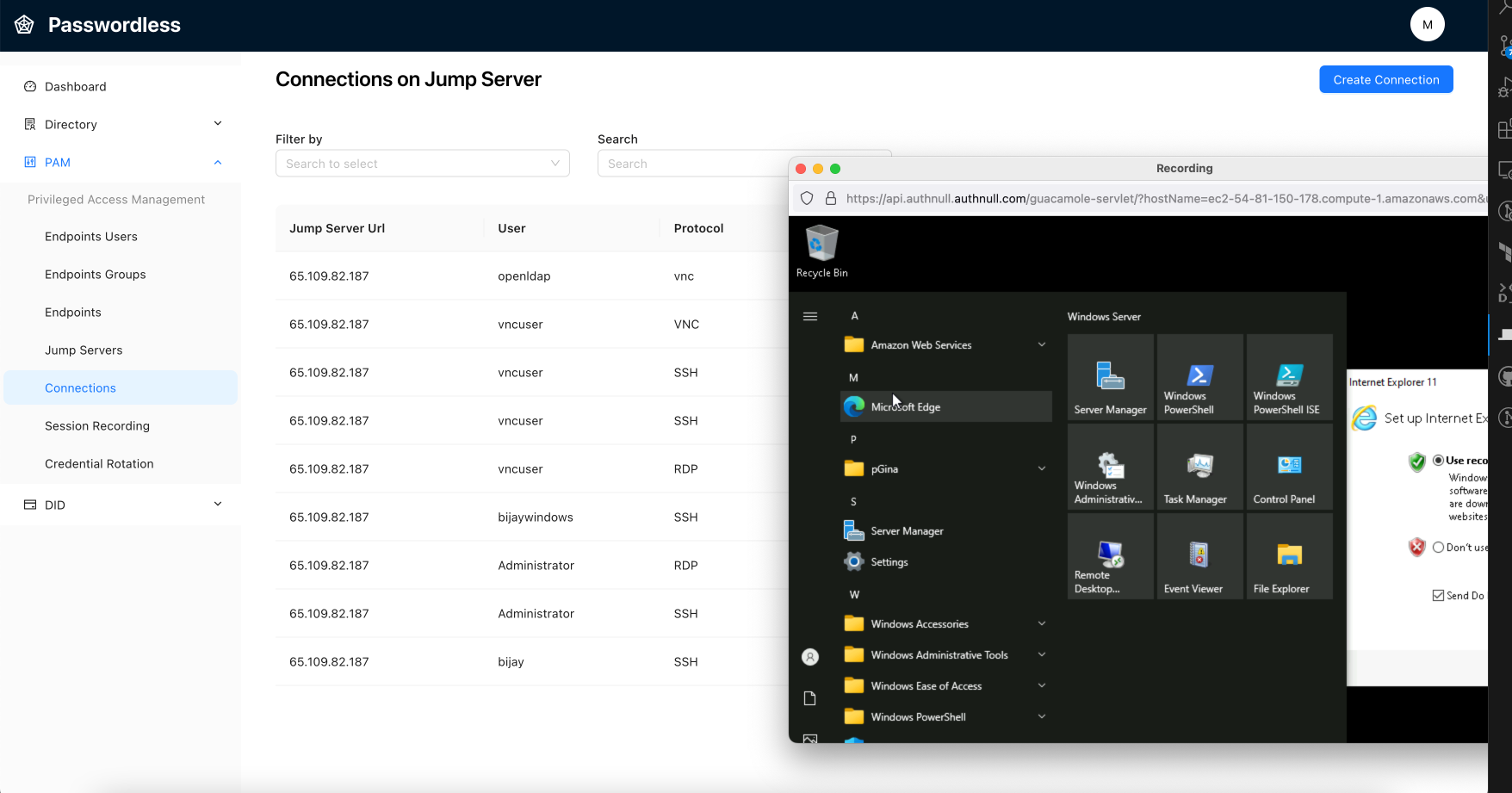
AuthNull delivers simplified endpoint privileged management (EPM) for your Windows and Linux servers
Sync users 2-way, install configure and manage services remotely, manage local privileged accounts, setup credential policies and rotate policies and much more.