Get A Demo
Begin your journey to passwordless
Comprehensive and Simplified Endpoint security
AuthNull provides comprehensive endpoint security needs

Begin your journey to passwordless
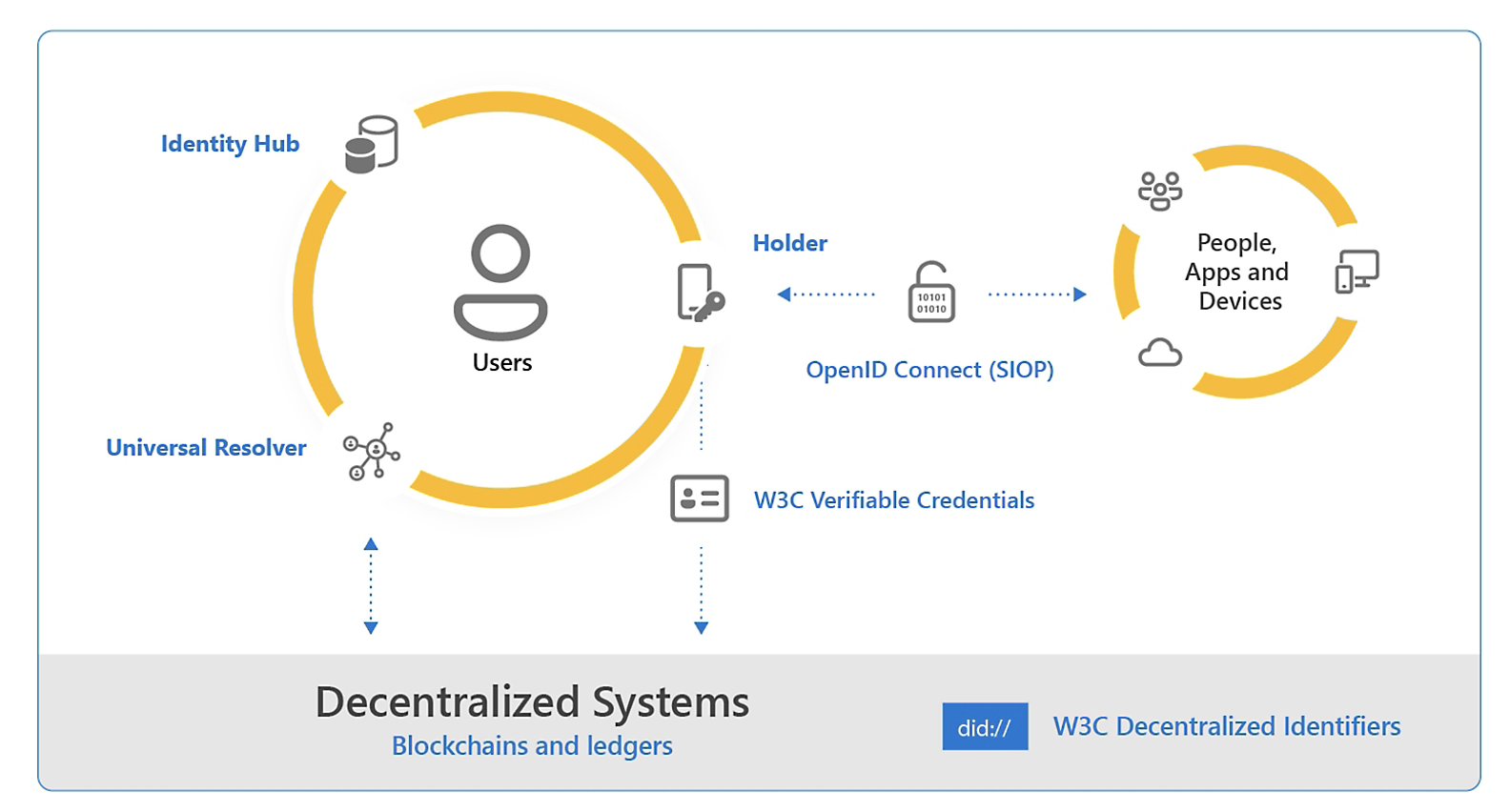
The federal government is undergoing a shift in technology, with decentralized identity (DID) emerging as a promising solution for improving identity and access management.
Read more
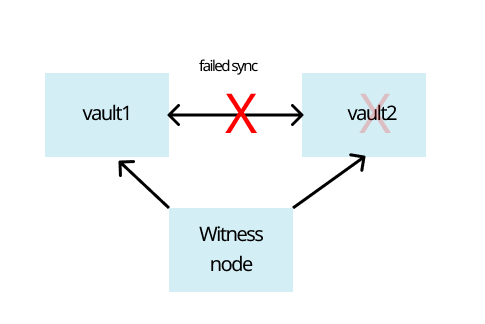
AuthNull: The PAM solution that's immune to split brain problems that come with traditional PAM solutions. Read the blog to learn more.
Read more
We see AI being central in reducing the IT workload in managing identities, authentication and authorization and see AuthNull leading from the front on these initiatives.

Achieve FIPS compliance by adopting to a decentralised PAM solution eliminating passwords, improving usability, and reducing costs.
Read more

Decentralized identifiers (DIDs) are a new type of identifier that enables verifiable, decentralized digital identity. A DID refers to any subject (e.g., a person, organization, thing, data model, abstract entity, etc.) as determined by the controller of the DID.
Read more

Users need to own their identity. Something that they own, control and its available on their devices as opposed to managed by centralized platforms. This paradigm is called Self-Sovereign identity.

In this blog, we explain how passwords can be cracked and why central management of credentials is well past its prime
Read more
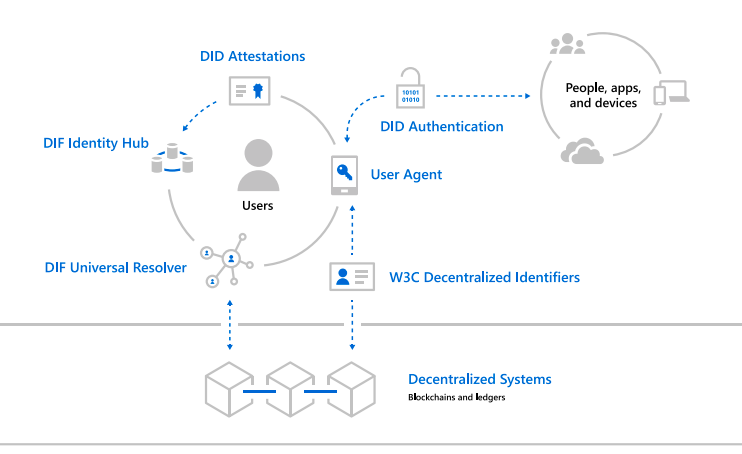
Decentralized identifiers (DIDs) are a new type of identifier that enables verifiable, decentralized digital identity. A DID refers to any subject (e.g., a person, organization, thing, data model, abstract entity, etc.) as determined by the controller of the DID.
Read more