Dynamic Authz
Dynamic Authorization Platform (PREVIEW)
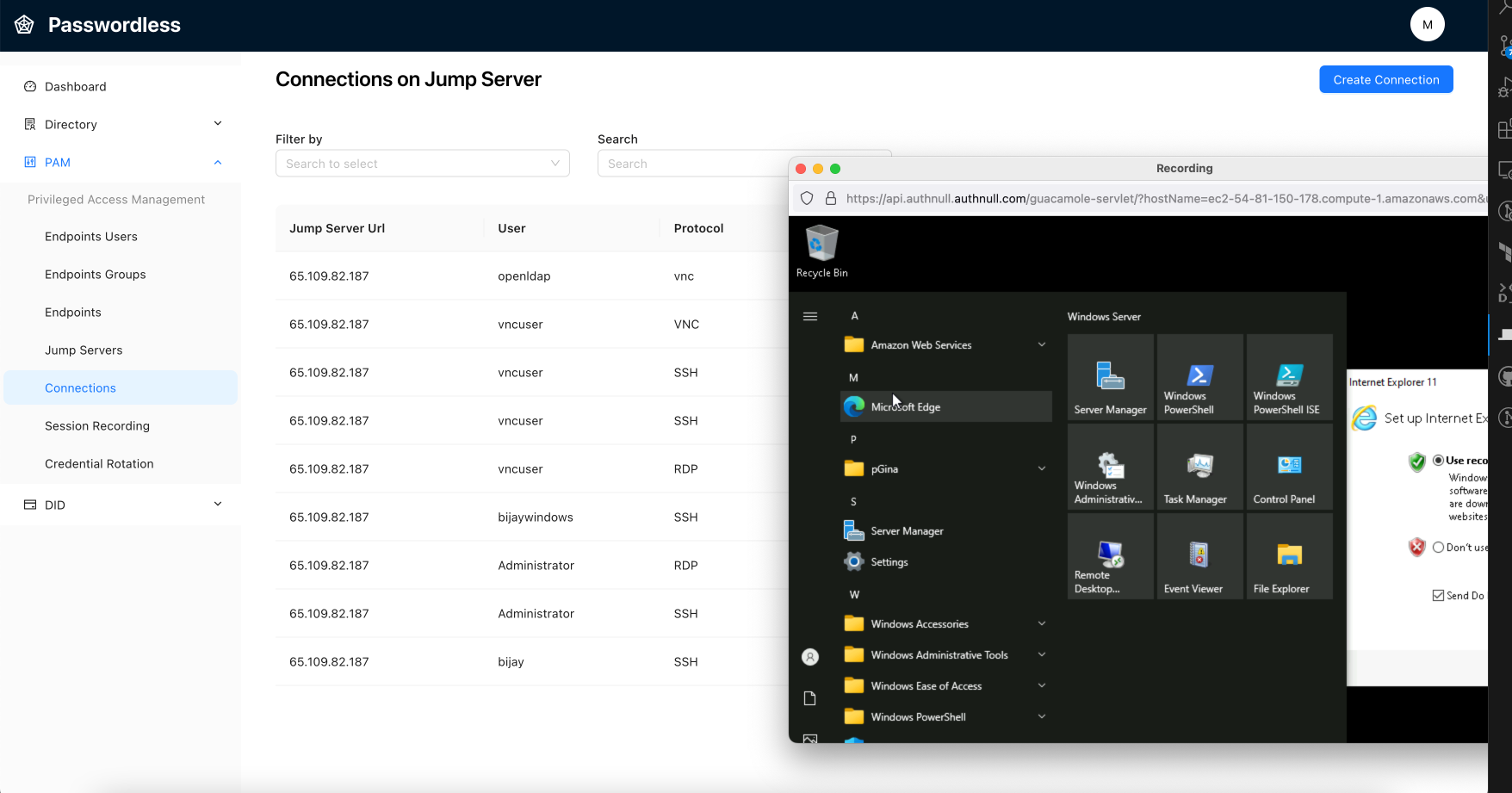
Provide rule based access with JIT entitlements. Reduce risk in privileged access
How does this work?
AuthNull enables Dynamic Authorization by modifying entitlements on the fly with rule based access
Endpoint logs are continously processed to provide a powerful solution that enables administrators to create rules that can be executed against endpoints.
Increase or decrease permissions on the fly.